Ignoring SSL Certificate Issues with cURL

Gabriel Manricks
Chief Architect, ClearX
Published: 1/31/2024
When making a request with cURL to a secured (HTTPS) endpoint, cURL will automatically verify the authenticity and validity of the certificate during the handshake before sending the request. There are times when you might want to bypass this check and tell cURL to make the request anyways; for example, on a development server with a self-signed certificate.
The Short Answer
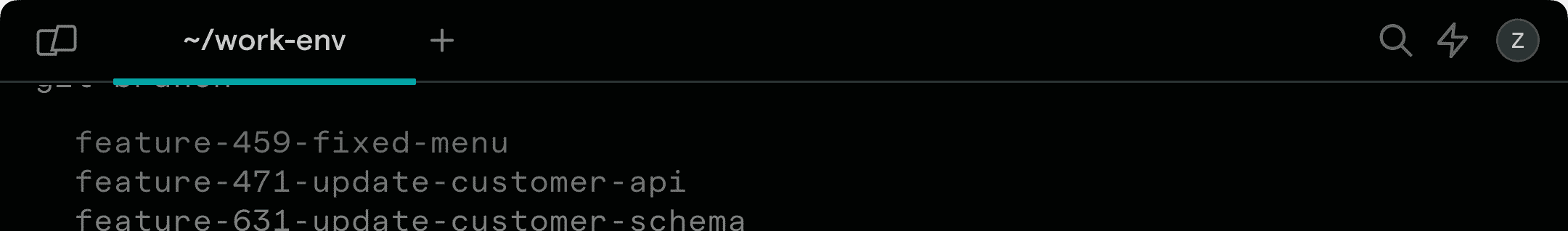
You can bypass the certificate verification by adding the -k or --insecure flag to your request.
$ curl https://expired.badssl.com/
curl: (60) SSL certificate problem: certificate has expired
$ curl https://expired.badssl.com/ -k
<!DOCTYPE html>
…
</html>
…
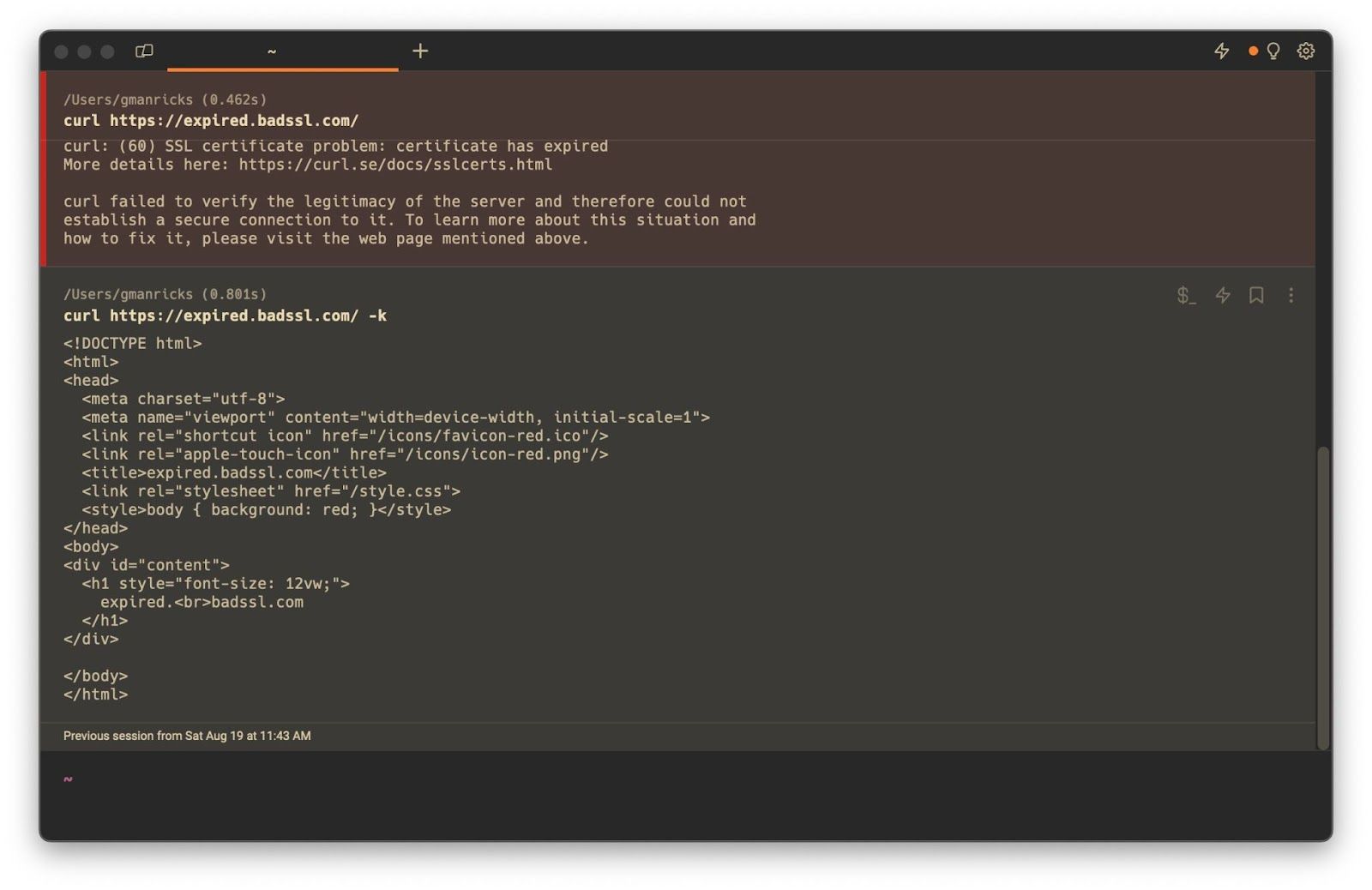
Easily recall this command with AI
If you are using Warp, you can get to this request using the AI Command Search by typing # and then curl ignore ssl
# curl ignore ssl
Bypassing an insecure proxy with cURL
There are situations where you are making a cURL request through a proxy server and the problematic certificate is not from the final endpoint you are requesting, but it is rather a problem with the intermediate proxy-server’s certificate.
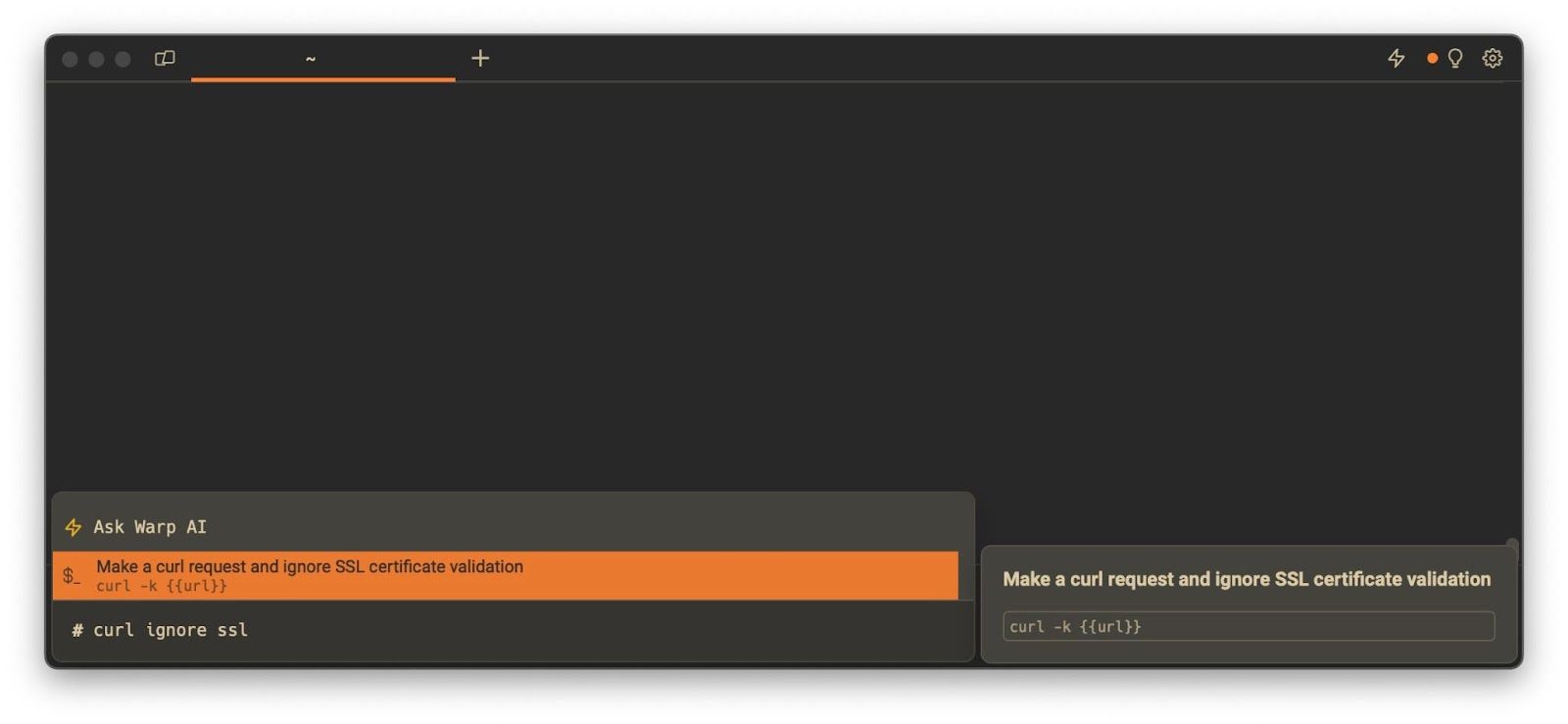
In situations like this, you can use the --proxy-insecure flag together with the -k / --insecure flag above to bypass the security checks.
For example, if you start a local HTTPs proxy with something like mitmproxy:
$ mitmproxy
It should open a local proxy server, and you can then see that trying to make a request through it, even to a legitimate endpoint, will give an error:
$ curl https://google.com --proxy https://localhost:8080
curl: (60) SSL certificate problem: unable to get local issuer certificate
By adding the two flags, we can get the request to go through:
$ curl https://google.com --proxy https://localhost:8080 --proxy-insecure -k
<HTML><HEAD><meta http-equiv="content-type" content="text/html;charset=utf-8">
<TITLE>301 Moved</TITLE></HEAD><BODY>
<H1>301 Moved</H1>
The document has moved
<A HREF="https://www.google.com/">here</A>.
</BODY></HTML>
Disabling certificate verification system-wide
There are some situations where you may want to disable this certificate verification system-wide. For example, if the curl requests in question are being generated by some script (Python, PHP, etc.) and it would be a lot of effort to update all the locations making requests.
In situations like these, if you need an easy way to temporarily disable SSL verification system-wide, you can add insecure and optionally proxy-insecure to your ~/.curlrc file.
insecure
proxy-insecure
Adding them to your ~/.curlrc will have exactly the same effect as passing them as command line options, so you can use whichever option better fits your situation.
Beware of potential security concerns
When you bypass cURL’s verification of the TLS / SSL certificate, TLS / SSL becomes less able to secure your connection. This leaves you exposed to risks like man-in-the-middle attacks, where, for example, a malicious actor can gain access to your traffic and impersonate the server you are trying to reach by returning its own certificate instead of the real one. This would allow the malicious actor to decrypt your requests.
So this workaround should only be used in situations where you know why the certificate is invalid and you temporarily want to make the request despite the associated risks. Some typical examples of this situation could be:
- Sending a request to a development server that has a self-signed certificate
- Your certificate just recently expired and you want to make the cURL request before getting it renewed
A more robust solution for situations like the above, where you want to work with a self-signed certificate, would be to make cURL trust your personal root certificate authority’s (CA) certificate, and leave verification on. This would allow you to still make the request, but have the protection against issues like the attack discussed above.
To do this, you will need the root CA certificate which signed your server’s certificate. In the mitmproxy example from above, you can get the certificate using:
$ curl http://mitm.it/cert/pem --proxy https://localhost:8080 -k --proxy-insecure > cacert.pem
You can then use that certificate in other cURL requests as follows:
$ curl https://google.com --proxy https://localhost:8080 --proxy-cacert ./cacert.pem --cacert ./cacert.pem
To read more about retrieving and using root CA certificates you can take a look at this post by Daniel Stenberg, one of the maintainers of cURL.
Written by

Gabriel Manricks
Chief Architect, ClearX
Filed Under
Related Articles
List Open Ports in Linux
Learn how to output the list of open TCP and UDP ports in Linux, as well as their IP addresses and ports using the netstat command.

Count Files in Linux
Learn how to count files and folders contained in directories and subdirectories in Linux using the ls, find, and wc commands.

How to Check the Size of Folders in Linux
Learn how to output the size of directories and subdirectories in a human-readable format in Linux and macOS using the du command.

Linux Chmod Command
Understand how to use chmod to change the permissions of files and directories. See examples with various chmod options.

POST JSON Data With Curl
How to send valid HTTP POST requests with JSON data payloads using the curl command and how to avoid common syntax pitfalls. Also, how to solve the HTTP 405 error code.

Format Command Output In Linux
Learn how to filter and format the content of files and the output of commands in Linux using the awk command.
Create Groups In Linux
Learn how to manually and automatically create and list groups in Linux.
Switch Users In Linux
Learn how to switch between users, log in as another user, and execute commands as another user in Linux.
Remover Users in Linux
Learn how to remove local and remote user accounts and associated groups and files in Linux using the userdel and deluser commands.
Delete Files In Linux
Learn how to selectively delete files in Linux based on patterns and properties using the rm command.
Find Files In Linux
Learn how to find and filter files in Linux by owner, size, date, type and content using the find command.
Copy Files In Linux
Learn how to safely and recursively copy one or more files locally and remotely in Linux using the cp and scp command.